Companion to Intune –
Application Lifecycle &
Management Automation Platform
RealmJoin
Companion to Intune –
Application Lifecycle &
Management Automation Platform

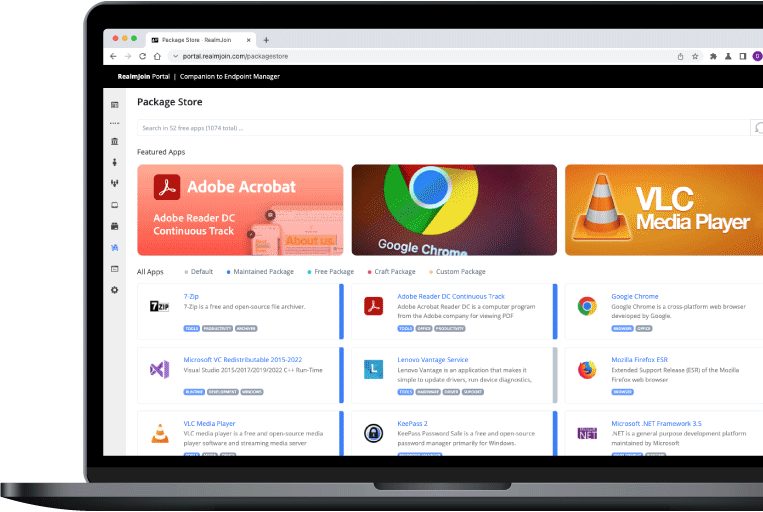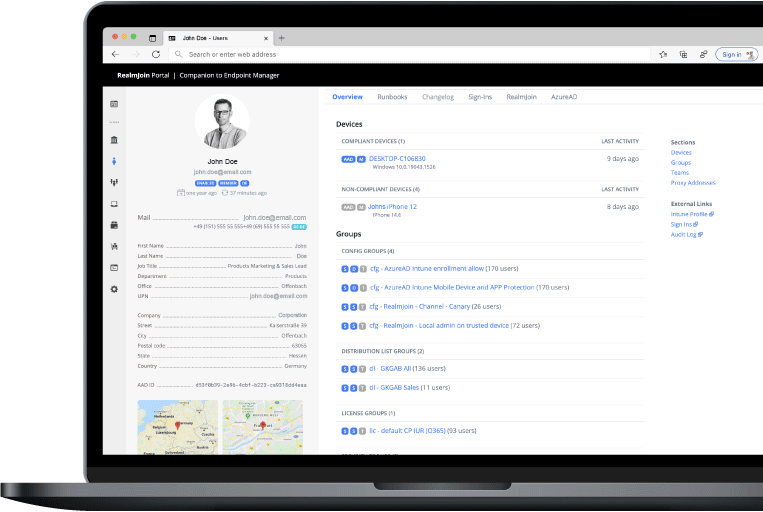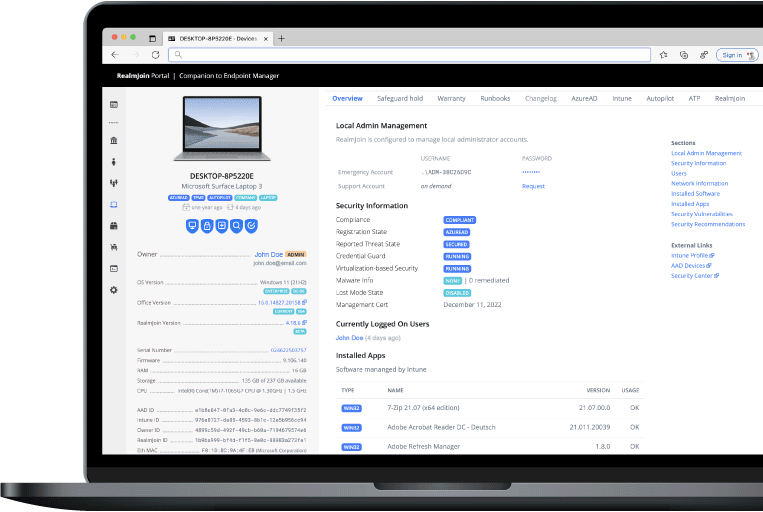
RealmJoin is the cloud born companion to Microsoft Endpoint Manager (Intune). It adds the missing pieces to provide an enterprise ready client management platform. RealmJoin improves the quality and reduces the efforts with nearly 1.000 pre-packaged standard applications for Intune, a modern package factory for custom applications and additional features like LAPS, remote support, Runbook automation and much more.
